Attacking Windows by Windows
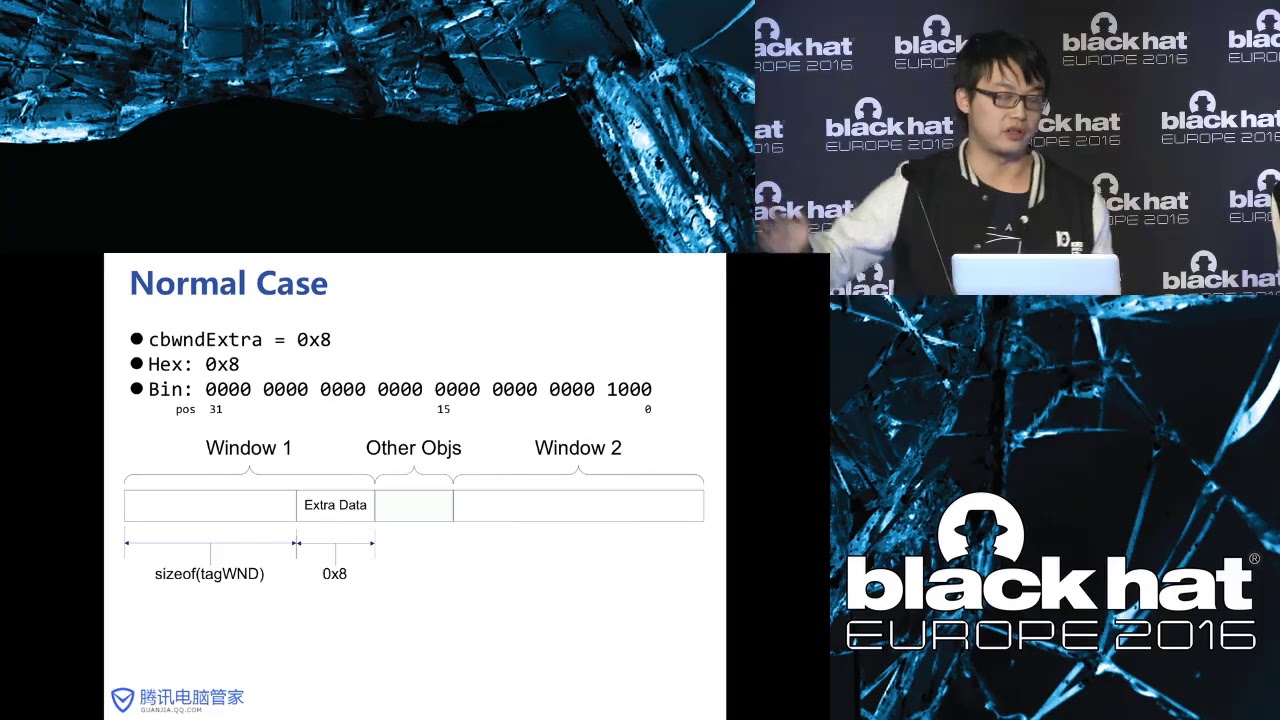
Since win8, Microsoft introduced a variety of exploit mitigations into Windows kernel, such as Kernel DEP,KASLR,SMEP; this made the exploit of Windows kernel much more difficult. Suppose that we find a Windows kernel 0day, which can change from 0 to 1, or 1 to 0 — how can we gain system privileges with it? This presentation will introduce a new common method which can be exploited from win2k to win10 to answer this question.
by Li Zhou, Yin Liang