Белые хакеры из Германии осуществили взлом автомобилей Tesla, получив доступ к заблокированным платным функциям. Соответствующая работа была проведена специалистами Технического университета Берлина, которые обнаружили уязвимость в системе электрокаров. Как сообщает издание TechCrunch, хакерам удалось активировать подогрев задних сидений в Tesla, функцию, которая изначально недоступна без подписки стоимостью около 300 долларов. Однако стоит отметить, что для […]
Мировое сообщество по информационной безопасности негативно отнеслась к предложению о полном отказе от терминов black hat и white hat. Все началось 3 июля, когда вице-президент корпорации Google, руководитель направлений Google Play и Android Security Девид Кляйдермахер сообщил, что не будет выступать на конференции Black Hat USA. Девид Кляйдермахер отказался выступать на конференции, которая была запланирована […]

At the close of this year’s conference, join Black Hat Founder Jeff Moss and members of the esteemed Black Hat Review Board for an insightful conversation on the most pressing issues facing the InfoSec community. This Locknote will feature a candid discussion on the key takeaways coming out of Black Hat Europe and how these […]
Designing, deploying, and securing an enterprise network is a stressful job when you have time, budget, and resources. But what about when all of those things are limited? This session will cover the lessons learned in over more than a decade of running the Black Hat network. We’ll talk about what makes the network tick, […]
by Stefano Zanero, Associate Professor, Dipartimento di Elettronica, Informazione e Bioingegneria So, you tasted a little of the Black Hat environment, and you want to end up on the stage next year? In this short session, Review Board member Stefano Zanero will go through some of the key errors found in the record number of […]
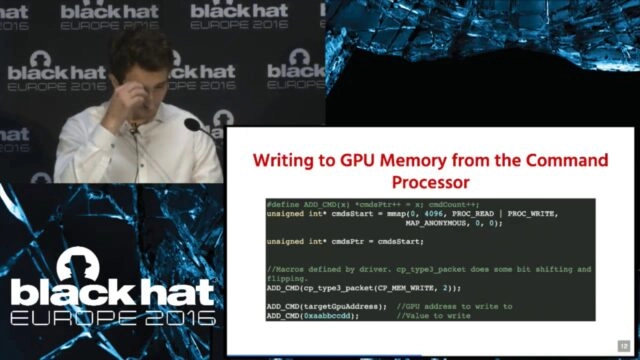
GPUs are found in millions of devices, allowing for stunning imagery to be generated on phones, tablets, and televisions. However, if we take a deeper look at how GPUs are programmed, the overall picture becomes much more bleak. GPUs directly accessing CPU memory, sensitive images not being cleared from graphics memory, and thin graphic APIs […]
At the close of Black Hat Europe 2016, Black Hat Founder Jeff Moss and members of the esteemed Black Hat Review Board, Chris Wysopal, Daniel Cuthbert, and Sharon Conheady discuss the most pressing issues facing the InfoSec community. This Locknote features a candid discussion on the key takeaways coming out of Black Hat Europe and […]
When serious vulnerabilities like ShellShock or ImageTragick are revealed, the announcement is often accompanied by PoC code. But what are the real payloads that attackers attempt to use when exploiting these vulnerabilities? Seeing the real payloads people use is often very difficult, but CloudFlare is in a unique position. By offering security services to over […]